December closed out 2025 as one of the year's most active months for ransomware, with established operations maintaining momentum and edge networking equipment representing a key exploitation target. Qilin and Akira continued to dominate deployment activity, with concentrated targeting of Manufacturing and Production, Construction and Engineering, and Technology sectors. These industries face heightened risk due to operational dependencies and supply chain complexity that create significant leverage for extortion.
Throughout December we saw widespread exploitation of authentication and edge device vulnerabilities, including critical flaws in Gladinet CentreStack, Fortinet FortiCloud SSO, and WatchGuard Fireware OS. This month's Case Study examines LockBit 5.0, which showed significant activity in December and warrants monitoring heading into 2026. The Resilience Spotlight provides guidance on controls for defending against both emerging and long-standing ransomware threats.
Phishing emails, VPN vulnerabilities, lack of Multifactor Authentication (MFA), software flaws, drive-by downloads, and social engineering remain the most frequently observed initial access points for ransomware attacks.
Ransomware activity increased in Q4 2025 compared to previous quarters, with December ranking as one of the most active months of the year. Qilin and Akira remained the most actively deployed ransomware throughout all of 2025, with over 1,500 victims published to their leak sites this year. Both groups operate under ransomware-as-a-service models that continued to drive a significant portion of activity through widespread affiliate deployment.
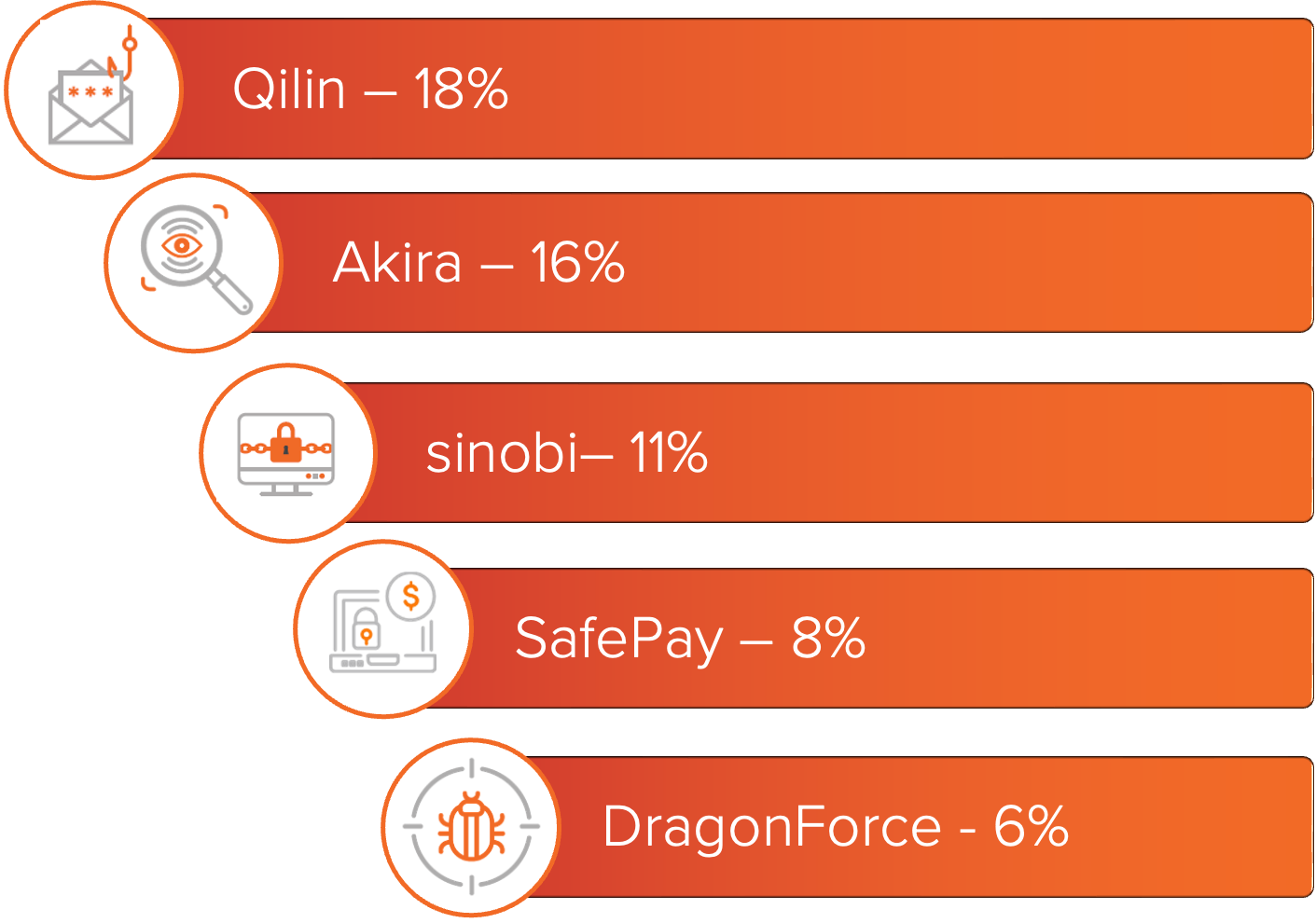
Figure 1: Top ransomware variants based on number of known victims.
The ransomware and industry rankings below are based on observed ransomware data leak site (DLS) activity for impacted organizations in the United States.
For a deeper look into these groups, MOXFIVE has published Threat Actor Spotlights on Qilin, Akira, Sinobi, SafePay, and DragonForce.
Manufacturing and Production remained the most impacted industry in December, continuing a trend observed throughout 2025. Threat actors continue to target this sector due to the high impact that business interruption can have and the use of connected supply chains that create multiple paths for initial access. Technology was the second most impacted industry, as service providers and software platforms often maintain direct integration with client networks and cloud environments, increasing the potential impact of a single intrusion.
Technology, Healthcare, and Retail and Hospitality also saw consistent ransomware activity in December. Technology organizations remained attractive targets as service providers and software platforms often
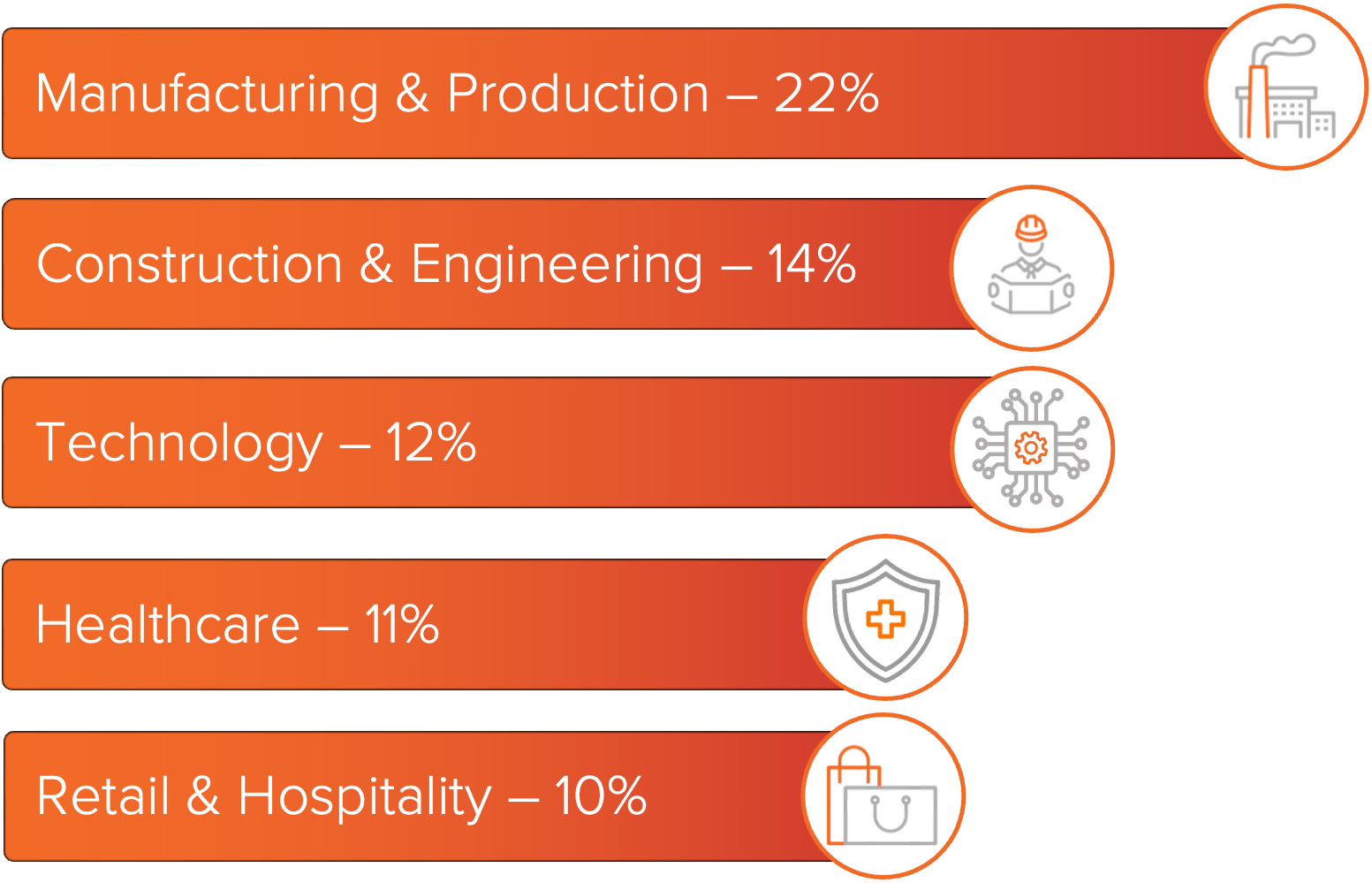
Figure 2: Top industries impacted by ransomware this month.
maintain direct integration with client networks and cloud environments, increasing the potential impact of a single intrusion. Healthcare organizations continued to face attacks due to the sensitivity of patient and operational data and their limited tolerance for sustained outages. Retail and Hospitality incidents often involved organizations that process payment data or operate distributed physical locations, exposing point-of-sale systems and supporting infrastructure.
Across these industries, Qilin activity spanned most sectors throughout December. Akira activity was primarily concentrated in Manufacturing and Production as well as Construction and Engineering. The remaining top variants were distributed across multiple industries, with no single sector dominating their targeting patterns.
Despite a major law enforcement disruption in early 2024, the LockBit ransomware operation persisted, with operators launching LockBit 5.0 in September 2025. In December, over 80 victims were posted on the LockBit 5.0 leak site, though some postings may include re-published data from earlier LockBit operations. Victims spanned multiple industries with Technology and Manufacturing & Production being the most heavily impacted sectors. While United States organizations represented the highest percentage of victims by country, targeting was significantly more geographically diverse compared to other leading ransomware operations, with substantial activity concentrated in Brazil, Germany, Turkey, and France. Threat actor group targeting pattern warrants close monitoring as affiliate recruitment expands, and operational focus may shift more heavily toward United States-based entities.
LockBit 5.0 introduced the following new enhancements:
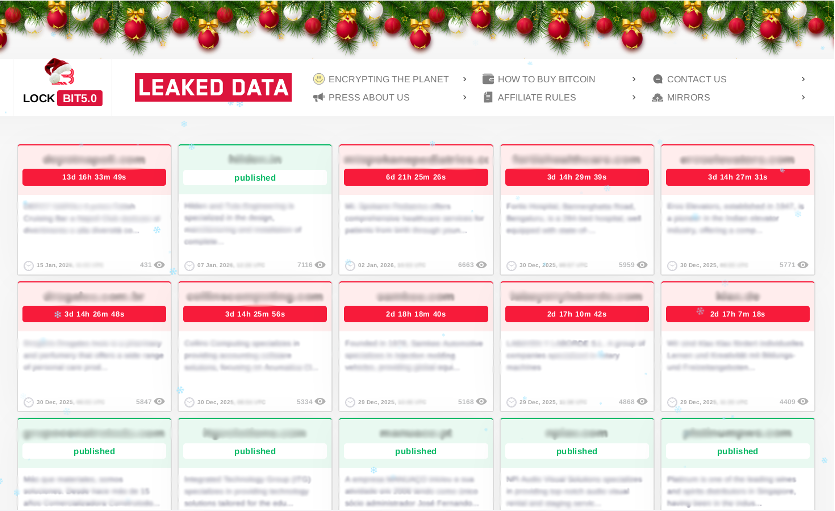
Figure 3: LockBit 5.0 Data Leak Site.
LockBit first emerged in 2019 and quickly grew to become one of the largest ransomware-as-a-service operations globally. Following Operation Cronos in February 2024, which seized infrastructure, exposed affiliate data, and resulted in several arrests, key members of the operation evaded capture and kept LockBit alive. In September 2025, LockBit operators officially announced LockBit 5.0 on underground forums, marking the operation's sixth anniversary and calling for new affiliates to join. The variant's modular architecture and improved evasion capabilities signal the operation's continued viability as a ransomware threat heading into 2026.
LockBit 5.0 demonstrates how established ransomware operations can maintain continuity and resume large-scale campaigns following infrastructure disruption. The variant's cross-platform capabilities, enhanced evasion mechanisms, and mature affiliate network represent the type of persistent, well-resourced threat that can impact organizations across industries and geographies. Resilience in this environment depends on a focused set of controls that reduce the impact of ransomware operations regardless of whether they are newly emerged variants or long-standing groups with proven track records.
How MOXFIVE Can Help
MOXGUARD: Strategic advisory including AD/identity assessments, CVE alerting prioritized to active ransomware exploitation, guidance on segmentation and backup hardening, tabletop exercises with response playbooks, and pre-positioned incident response.
Professional Services: Control validation through EDR coverage assessments, purple team exercises, network segmentation reviews, backup immutability and restoration testing, external attack surface reduction, and SIEM/XDR detection engineering. Our team has handled hundreds of ransomware cases against Qilin, Akira, LockBit, and other active operations, aligning preventive, detective, and recovery controls to current threat actor TTPs.
Contact us at 833-568-6695 or email our team directly at incident@moxfive.com.