Ransomware activity remained steady throughout June 2025, with Qilin and DragonForce emerging as the most active variants. Both groups appear to be absorbing former RansomHub affiliates following its disappearance earlier this year. Qilin continues to attract partners through a competitive commission model, while DragonForce has claimed credit for the RansomHub takedown in an effort to position itself as the preferred cartel infrastructure. Scattered Spider, known for its use of social engineering and post-exploitation tooling, has been linked to deployments of both variants in recent campaigns.
This report also reviews the disclosure of Citrix Bleed 2 (CVE-2025-5777), a critical vulnerability affecting NetScaler ADC and Gateway devices. While exploitation has not been confirmed, its similarities to the original Citrix Bleed and the release of proof-of-concept code have raised concern across the security community. The featured Case Study explores how delayed patching and token reuse can lead to credential-free access, while the Resilience Spotlight outlines key practices for hardening external infrastructure and managing session integrity.

Phishing emails, VPN vulnerabilities, lack of Multifactor Authentication (MFA), software flaws, drive-by downloads, and social engineering remain the most frequently observed initial access points for ransomware attacks.

Ransomware activity remained steady throughout June, with several established ransomware services continuing to account for the majority of victim postings across data leak (DLS) sites.
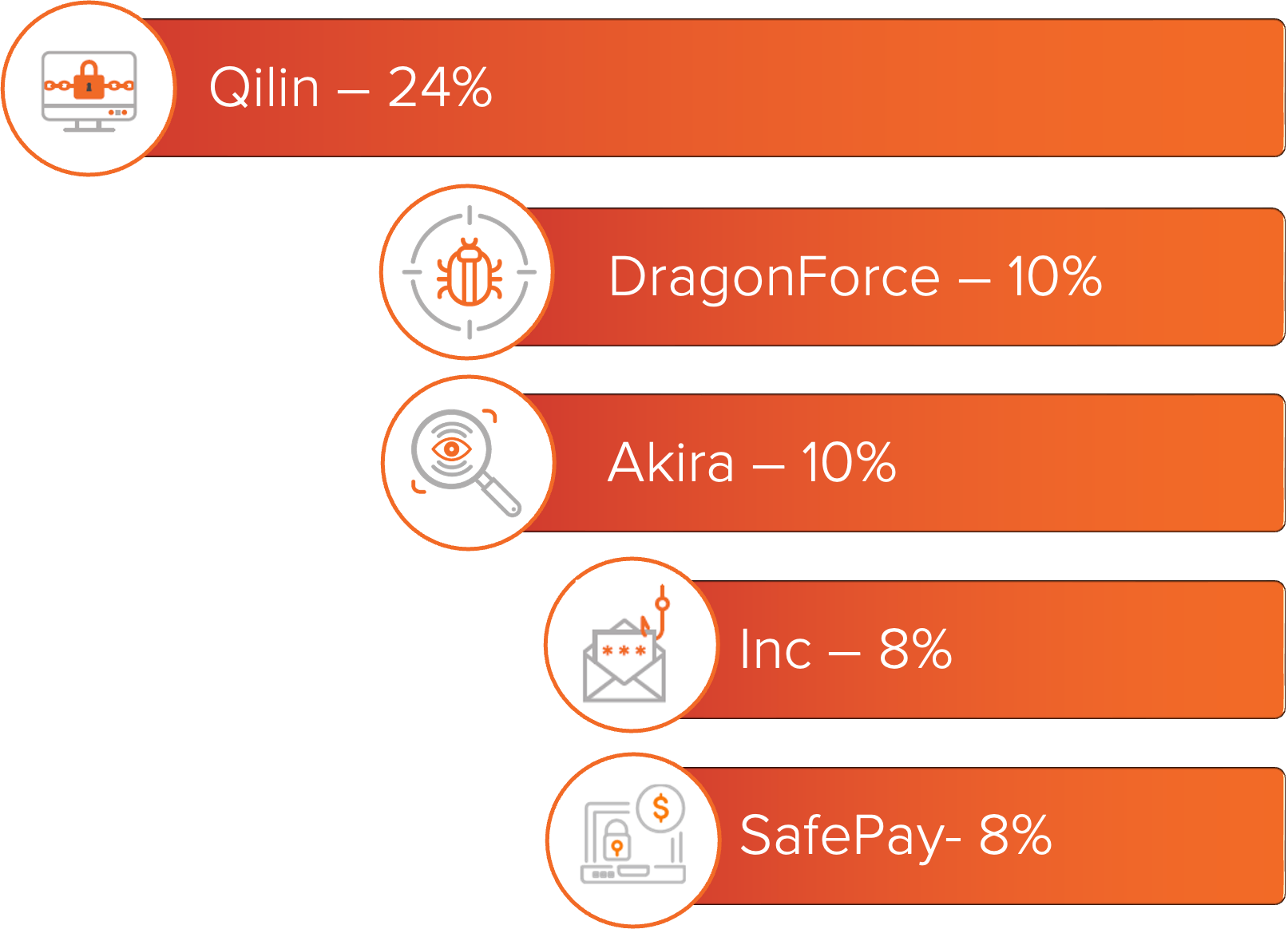
Figure 1: Top ransomware variants based on number of known victims.
The ransomware and industry rankings below are based on observed ransomware data leak site (DLS) activity for impacted organizations in the United States.
For a deeper look into these groups, MOXFIVE has published Threat Actor Spotlights on Qilin, Akira, and DragonForce.

Healthcare was the most impacted industry in June based on observed ransomware DLS activity. Manufacturing and Production followed closely and remains the most impacted industry overall in the first half of 2025, reflecting the continued success of ransomware operations against organizations in this sector.
The Technology and Finance industries ranked third and fourth, respectively. Both sectors experienced consistent impact, with multiple variants linked to successful compromises across enterprise environments.
Retail and Hospitality completed the top five sectors impacted. Scattered Spider activity contributed to increased impact in this sector, with the group initially compromising UK-based retailers before shifting toward U.S.
e-commerce and consumer platforms.
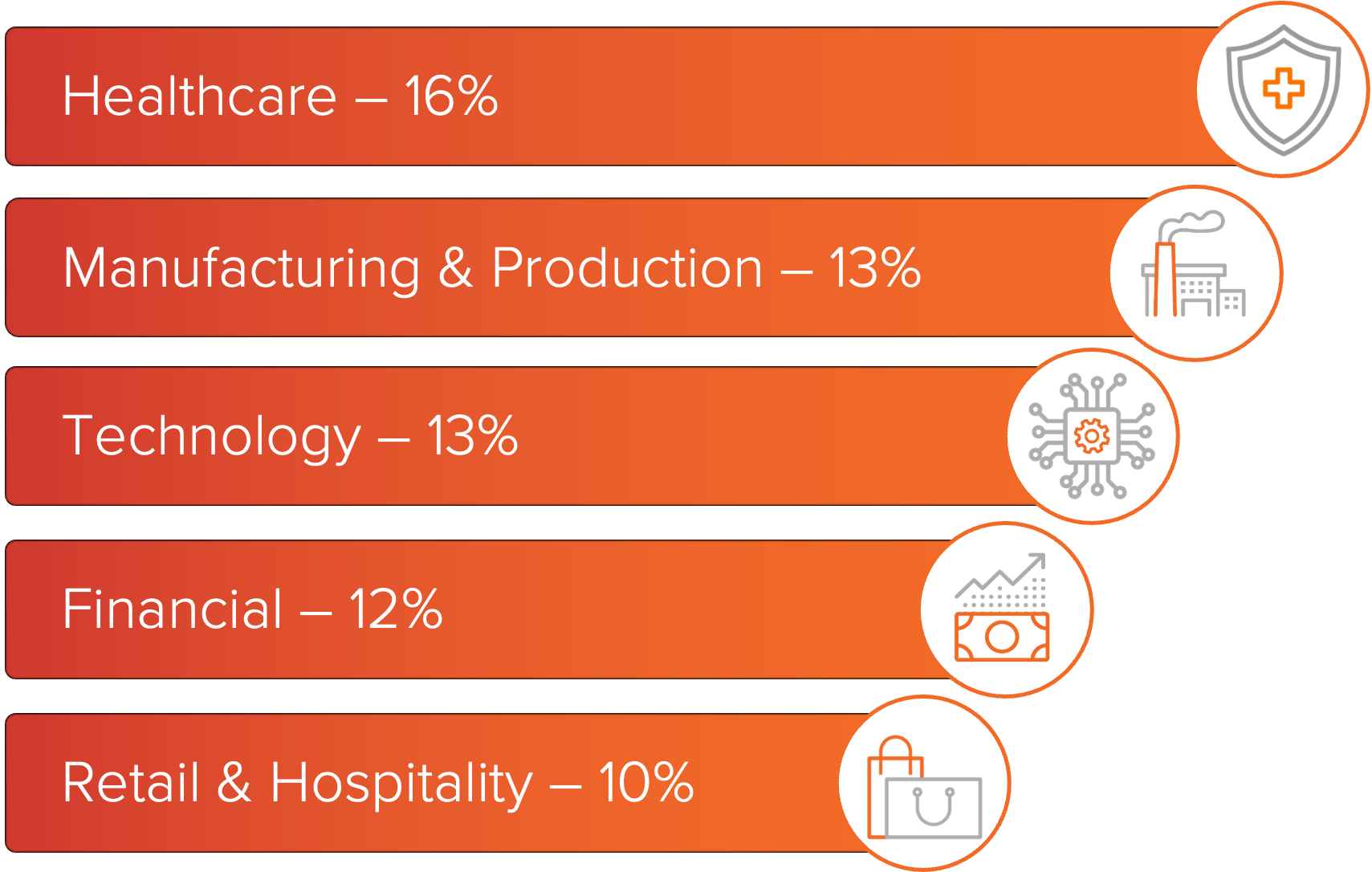
Figure 2: Top industries impacted by ransomware this month.

Citrix Bleed 2 and External Infrastructure Abuse
Keeping external-facing infrastructure fully patched remains critical, particularly for systems that authenticate users and manage access to internal environments. Unpatched edge appliances often serve as initial entry points for threat actors due to their accessibility and the high value of session and credential data processed through them. Delays in applying security updates continue to expose organizations to well-documented exploitation paths.
In 2023, Citrix disclosed CVE-2023-4966, later known as Citrix Bleed, a vulnerability in NetScaler ADC and Gateway devices that exposed session tokens. It was exploited shortly after disclosure by threat actors, including affiliates of LockBit and Medusa, to access enterprise networks. In June 2025, Citrix released a patch for CVE-2025-5777, referred to as Citrix Bleed 2, which enables similar token extraction through crafted POST requests. Proof-of-concept code was published within days, and while Citrix has not confirmed in-the-wild exploitation, multiple vendors have reported scanning activity and indicators of potential abuse.
As with the original Citrix Bleed, the concern is not just the technical severity of the flaw, but the exposure that follows. In the days following the June disclosure, numerous NetScaler devices remained exposed and unpatched. This mirrors the early warning signs seen in 2023, where failure to act promptly contributed to high-impact ransomware intrusions across healthcare, legal, and manufacturing sectors. Timely patching and session management are essential to reducing exposure.

Hardening Edge Services and Session Hygiene
Vulnerabilities in edge infrastructure carry elevated risk due to their exposure and role in user authentication. When exploited, flaws like Citrix Bleed 2 can allow attackers to bypass multifactor authentication and gain access without valid credentials, often without triggering traditional indicators of compromise. The following practices can help reduce exposure and mitigate impact:
Proactive patching, session management, and reduced exposure at the edge are critical to preventing credential-free access in the wake of high-impact vulnerabilities like Citrix Bleed 2.
Join us on Wednesday, July 30th at 2pm ET for our Mid-Year Ransomware Briefing where we'll dissect the latest developments and key trends for cyber incidents so far this year and provide practical strategies to strengthen your defenses for the remainder of 2025.
Register Today!
Need Help Now? Whether you need help responding to an incident or are just trying to better prepare for one, we can help. Contact us at 833-568-6695 or email our team directly at incident@moxfive.com.