Every month, we take a look at a current ransomware threat actor. If you would like to receive this via email each month, click below to subscribe to the MOXFIVE mailing list.
Additional Threat Actor Spotlights are available on our Resources page >>
INC Ransom is a ransomware group first observed in 2023 that operates under a Ransomware-as-a-Service (RaaS) model. The INC RaaS model allows affiliates to deploy the ransomware, most often using double-extortion tactics that combine data theft with system encryption. Encrypted files are commonly renamed with the “.inc” extension, and ransom notes direct victims to initiate negotiations. MOXFIVE has supported numerous investigations involving this ransomware since its emergence and continues to track the group’s activity and evolving tactics.
As of this report, more than 200 victims have been published to INC’s leak site in 2025. In July 2025, INC was the most deployed ransomware based on the number of victims posted. In 2024, researchers reported that INC’s source code was offered for sale on underground forums. Elements of that code have since been linked to the development of Lynx ransomware, suggesting a strong overlap between the two families.
The following sections provide an overview of INC’s industry targeting, geographic distribution, initial access techniques, leveraged vulnerabilities, encryption behaviors, and tooling observed in recent campaigns.
Figure 1: INC Ransom data leak site.
Key Highlights
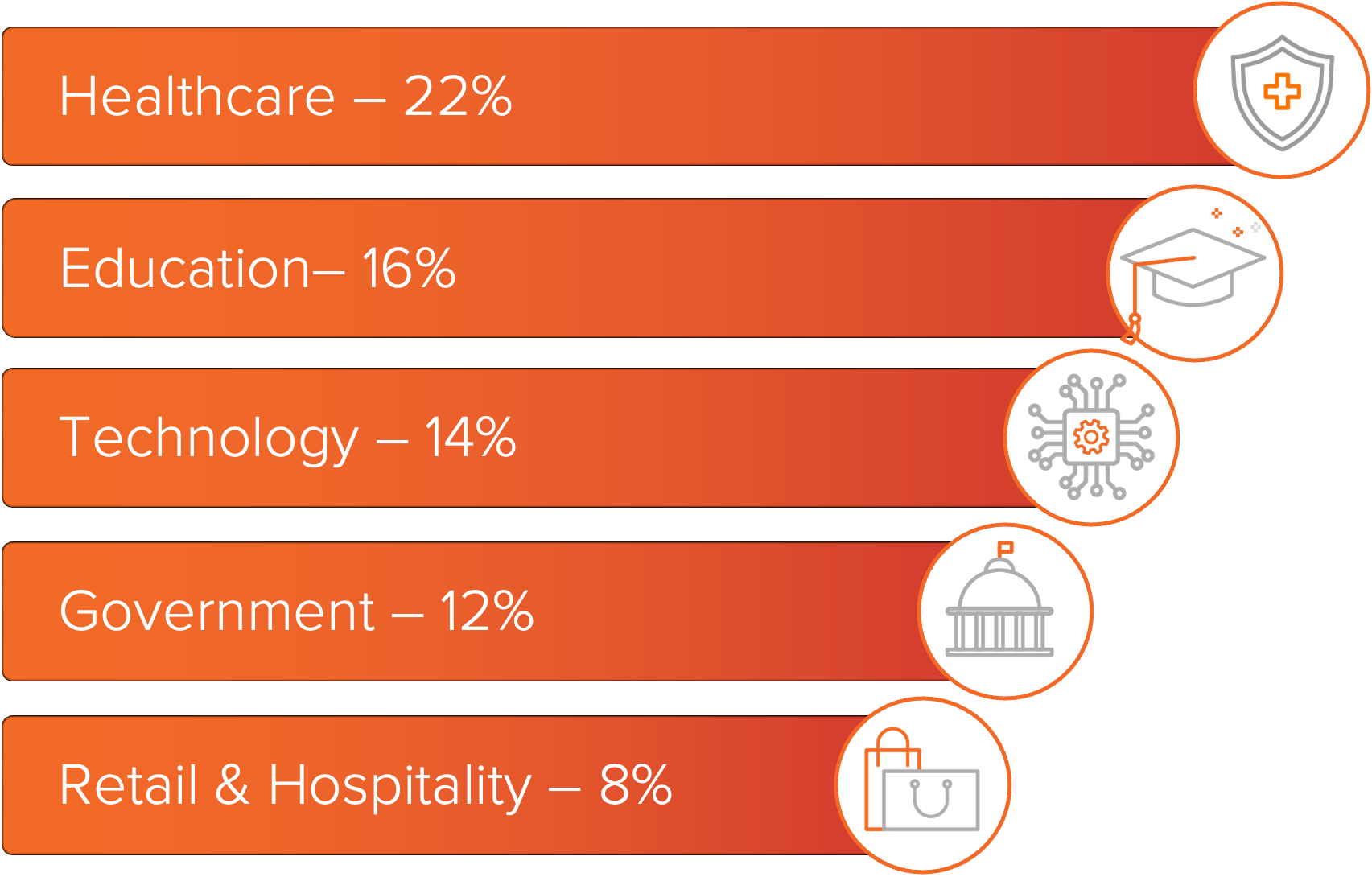
Threat actors deploying INC ransomware most frequently impacted healthcare organizations between January and August 2025. Education and technology followed, with government entities also among the top victims. Retail and hospitality organizations were less common but still represented within the top five. Other industries were also impacted at lower levels.
More than half of the victim organizations published by INC Ransom this year have been located in the United States. Canada and Germany were the next most impacted countries. Additional victims have been observed across other regions, though at lower levels of activity.
The observations below are based on incidents attributed to INC Ransom from January 2025 through August 2025.
Threat actors deploying INC ransomware have relied on multiple techniques to establish access to victim environments. Incidents show the use of phishing, credential abuse, and exploitation of public-facing applications and services.
INC ransomware employs a double-extortion model, combining data theft with system encryption to pressure victims. Encrypted files typically receive the .inc extension, and ransom notes often titled INC-README.txt or INC-README.html are dropped on affected hosts. The ransomware also modifies the desktop background, and, in some cases, ransom notes have been printed by connected printers. Different variants of INC ransomware have been developed for both Windows and ESXi, with the latter containing scripts to terminate virtual machines before encryption.
Prior to encryption, operators commonly stage data with utilities such as 7-Zip or WinRAR. Exfiltration is then carried out using tools like MEGASync or Rclone, which are configured to transfer stolen files to threat actor-controlled cloud storage accounts.
INC ransom demands have ranged from tens of thousands of dollars to as high as several million. Demands are typically scaled to the victim’s revenue, organizational size, and the sensitivity of exfiltrated data, with higher impact intrusions resulting in larger payment requests.
INC campaigns commonly use native utilities and widely available tools to run payloads, escalate privileges, move laterally, and exfiltrate data. The examples below reflect notable tactics observed in recent activity.
INC ransomware continues to be a leading ransomware service in 2025, supported by affiliates who rely on standard utilities and well-practiced intrusion methods. Given that INC was the most deployed ransomware based on leak site activity in July 2025, we expect INC will likely remain a top threat in the months ahead. MOXFIVE has responded to numerous incidents involving this group and anticipates continued engagements as affiliates maintain steady operations across sectors.
If you would like to know more or need assistance with incident response efforts, please contact us at 833-568-6695 or email our team at incident@moxfive.com.