Every month, we take a look at a current ransomware threat actor. If you would like to receive this via email each month, click below to subscribe to the MOXFIVE mailing list.
Additional Threat Actor Spotlights are available on our Resources page >>
LockBit is back in the spotlight, and LockBit 5.0 shows the operation has not slowed down. The operators are pushing a refreshed, holiday-themed leak site and an affiliate-driven ransomware model built for scale. MOXFIVE has responded to recent incidents where LockBit 5.0 was deployed, giving us current visibility into how it is being used. This report breaks down LockBit’s evolution, what the operators advertise in their own operation materials, what MOXFIVE has observed in recent engagements, and where LockBit 5.0 is being deployed across industries and countries.
LockBit first emerged in 2019 and was initially tracked as ABCD ransomware after early versions appended the “.abcd” extension to encrypted files. The LockBit name gained traction the following year as operators formalized the brand and began scaling the operation through a Ransomware-as-a-Service (RaaS) model supported by a leak site and double extortion pressure. Under this model, deployment is typically carried out by LockBit affiliates using tooling and infrastructure provided by LockBit operators.
From 2021 through 2023, LockBit released multiple new versions with major updates, including expansion beyond Windows into Linux and ESXi-targeting tooling. In 2022, the LockBit 3.0 builder leak changed the landscape by enabling versions of the ransomware to be generated and deployed outside of the LockBit affiliate program. In February 2024, Operation Cronos disrupted LockBit infrastructure and seized parts of its online presence. LockBit operators still attempted to re-establish the program following that disruption, including promoting a new major version commonly referenced as LockBit 4.0, sometimes referred to as “LockBit Green.” Late 2025 activity tied to the LockBit brand then included the introduction of LockBit 5.0, showing the operation continued to iterate and remain active despite sustained law enforcement pressure.

LockBit 5.0 represents the most recent version of a ransomware operation that has continued to retool through disruption and scrutiny. MOXFIVE has responded to recent incidents where LockBit 5.0 was deployed, which gives us direct insight into how threat actors are deploying this variant in current ransomware campaigns. We also conduct deep research into LockBit and the infrastructure it supplies through its affiliate program.
Due to LockBit operating as an RaaS, initial access can vary depending on the affiliate and the target. Common ransomware initial access patterns include exposed remote access and valid or weak credentials without MFA. Other paths include vulnerability exploitation, brute force activity, phishing, and leaked credentials. Most of these common initial access trends have already appeared in early cases where LockBit 5.0 was deployed. The bullet list below is pulled from LockBit operators’ published feature overview on their leak site.
The bullet list below is pulled from LockBit operators’ published feature overview on their leak site.
In addition to the features listed by LockBit, MOXFIVE has also observed the following:
Since the release of LockBit 5.0, the holiday-themed leak site has remained active with frequent victim postings. Over the last two months, LockBit operators posted an estimated 100 victims. Across current postings, targeting is concentrated in Technology, Healthcare, Construction and Engineering, Financial Services, and Manufacturing and Production. Impact is also geographically diverse, with the United States representing the largest share of victims at approximately 23%, followed by activity across Brazil, Italy, Germany, and Mexico.
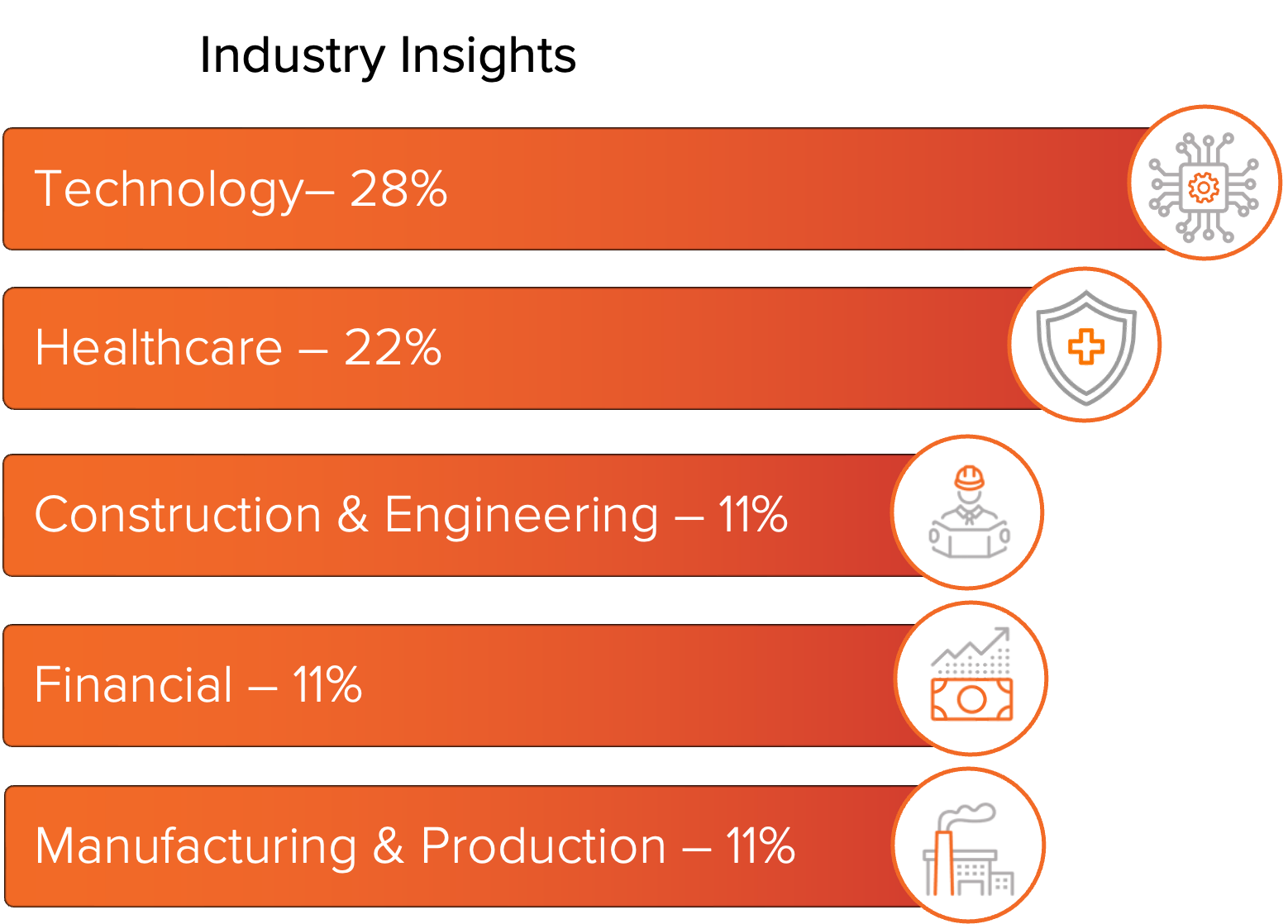
Figure 2: Industries impacted by LockBit 5.0.
LockBit operators also publish affiliate program rules that define how affiliates are expected to select targets. In those rules, LockBit states affiliates are allowed to target high-impact organization types, including critical infrastructure, oil and gas, medical facilities, law enforcement, military installations, space organizations, and government entities. The same rules prohibit affiliates from targeting several post-Soviet countries, specifically Armenia, Belarus, Georgia, Kazakhstan, Kyrgyzstan, Latvia, Lithuania, Moldova, Russia, Tajikistan, Turkmenistan, Uzbekistan, Ukraine, and Estonia.
LockBit is positioned to remain a prominent ransomware threat through 2026. The operators are re-establishing the brand around LockBit 5.0 while marketing a structured affiliate program, published rules, and deployment options built for scale. That model lowers the friction for affiliates to adopt the ransomware, which increases the likelihood of repeated deployments across industries and regions. MOXFIVE has responded to recent incidents where LockBit 5.0 was deployed, and we expect the operation’s notorious brand, active recruitment, and continued development to sustain risk beyond the initial 5.0 rollout.
LockBit is proof that established ransomware operations can absorb disruption and continue deploying updated tooling. Resilience depends on controls that reduce the blast radius of credential compromise and lateral movement. Priorities include enforcing MFA and strong credential hygiene, restricting administrative pathways into virtualization platforms and backups, maintaining full EDR coverage with tamper protections, reducing external exposure, ensuring visibility into available log sources such as ESXi and vCenter, and validating recovery through routine restoration testing.
MOXGUARD: Strategic advisory including AD/identity assessments, CVE alerting prioritized to active ransomware exploitation, guidance on segmentation and backup hardening, tabletop exercises with response playbooks, and pre-positioned incident response.
Professional Services: Control validation through EDR coverage assessments, purple team exercises, network segmentation reviews, backup immutability and restoration testing, external attack surface reduction, and SIEM/XDR detection engineering.MOXFIVE supports organizations through ransomware readiness and response, including recent cases where LockBit 5.0 was deployed, aligning preventive, detective, and recovery controls to current threat actor tradecraft.
Contact us at 833-568-6695 or email our team at incident@moxfive.com.