Play, also known as Playcrypt, is a ransomware group active since 2022. The group has listed more than 900 victims on its leak site and continues to target organizations across North America, South America, and Europe. Messaging on the site states that Play is not an affiliate program, claiming there are 'no third parties who decide to do otherwise than their affiliate partners.' This indicates that Play does not operate as a Ransomware-as-a-Service but rather functions as a closed group of threat actors.
Play operators employ a double extortion model, exfiltrating sensitive data before encrypting systems to increase pressure during ransom negotiations. Victims are instructed to initiate contact via email, and ransom notes generally do not specify an initial demand. In some cases, operators have escalated pressure through phone-based threats directed at internal staff. These actions align with the more aggressive approach that this group takes towards extortion and negotiation. Play operators have deployed different versions of the ransomware, targeting both Windows and ESXi environments, allowing them to impact endpoint and virtual infrastructure.
In the first half of 2025, Play was among the most active ransomware groups, with more than 200 victims published on the group’s leak site. The following sections provide an overview of the group’s activity, including industry targeting, geographic impact, initial access techniques, and tooling.
Figure 1: Play data leak site.
Key Highlights
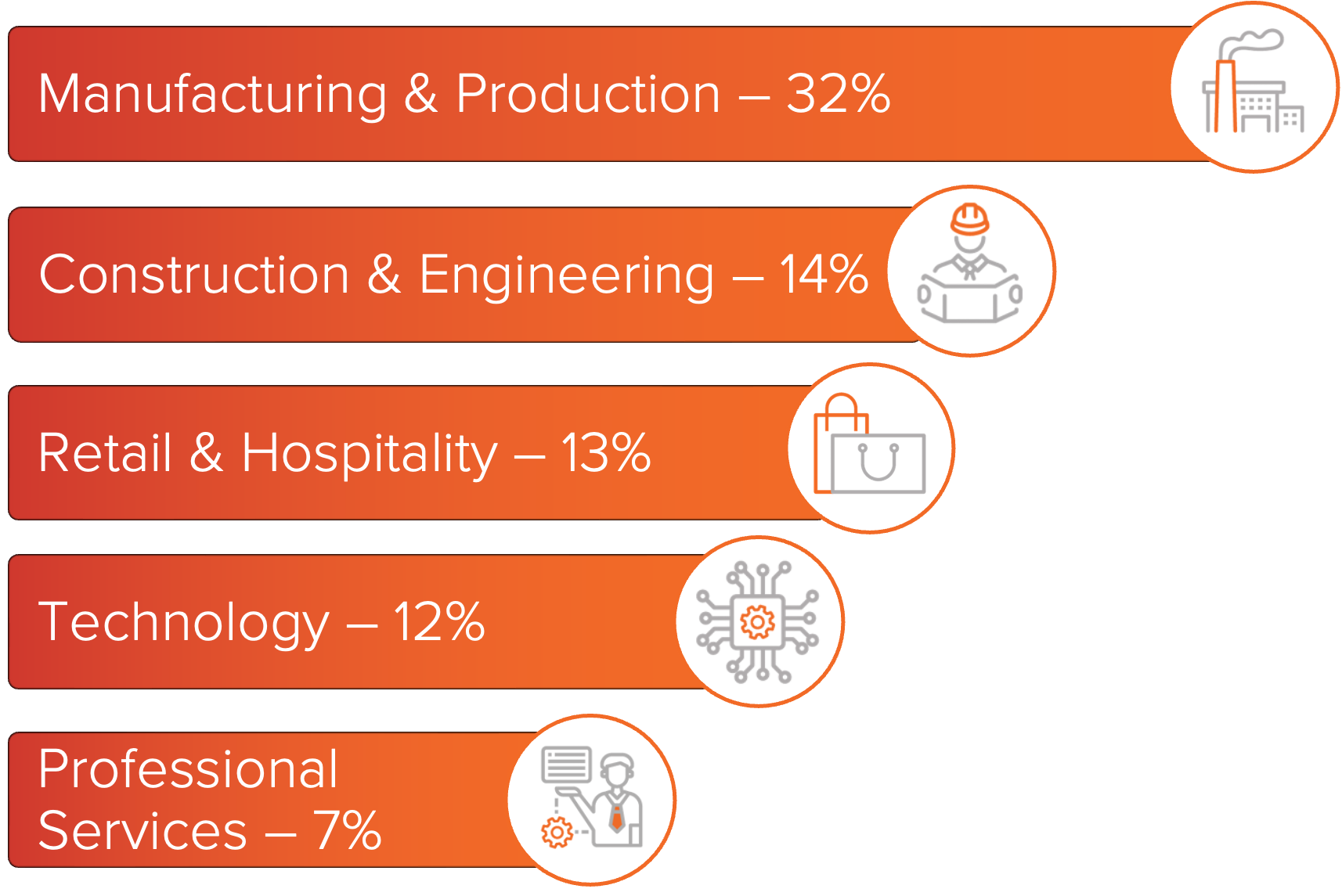
Play ransomware operators have primarily impacted organizations in the manufacturing and production industry. Other commonly affected sectors include construction and engineering, retail and hospitality, technology, and professional services, with additional victims observed across a wide range of industries.
The United States remains the primary target of the Play ransomware group, accounting for the majority of observed victims. Canada ranks second, with additional incidents reported across select countries in North America, South America, and Europe.
The observations below are based on incidents attributed to Play ransomware in the first half of 2025.
In many instances, the Play operators have gained initial access to victim environments through valid credentials, brute-force attacks, and the exploitation of vulnerabilities in remote access tools.
Play ransomware operators use a double extortion model, exfiltrating data from victim environments before encrypting systems to increase leverage during ransom negotiations. Victims are instructed to initiate contact via email, with no initial demand specified in the ransom note. In some cases, Play operators have also made phone calls to victims, threatening the release of stolen data and directing employees such as help desk or customer service personnel to relay ransom instructions.
Play operators have deployed different variants of the ransomware for Windows and ESXi environments, allowing the group to encrypt both endpoint and virtual infrastructure. The ESXi variant is known to shut down virtual machines before encrypting related files. Reporting also notes that both versions are recompiled per campaign and support additional runtime configurations that can adjust encryption behavior.
Play operators use a variety of publicly available tools and native system utilities to support key stages of their intrusions. The examples below reflect techniques observed during known incidents and highlight how the group maintains access, escalates privileges, and evades detection.
Play operators continue to employ a range of tactics that combine public tooling, credential abuse, and hands-on intrusion methods, reflecting an adaptable threat that requires sustained monitoring and a strong defensive posture.
MOXFIVE will continue tracking Play activity and supporting victim organizations through forensic investigations, recovery efforts, and long-term resilience planning.
If you would like to know more or need assistance with incident response efforts, please contact us at 833-568-6695 or email our team at incident@moxfive.com.