Every month, we take a look at a current ransomware threat actor. If you would like to receive this via email each month, click below to subscribe to the MOXFIVE mailing list.
SubscribeIn late 2025, administrators of the “scattered lapsus$ hunters” Telegram channel began promoting a new ransomware-as-a-service (RaaS) platform called ShinySp1d3r that they claim will operate under the Scattered LAPSUS$ Hunters (SLSH) name. Posts on this channel and a related leak site link SLSH to members and tradecraft from three established threat groups: Scattered Spider, LAPSUS$, and ShinyHunters. Most information about ShinySp1d3r and SLSH comes from these Telegram announcements, extortion posts on the leak site, and analysis of early samples shared with or obtained by researchers. Recent announcements suggest that this new ransomware may become operational in the near term.
MOXFIVE first reported on the alliance in August 2025, when the group launched a sophisticated social engineering campaign impersonating IT help desk staff to gain access to Salesforce data. Figure 1 shows the joint leak site that the group used to publish more than forty victims from this activity. The operation impacted organizations across multiple industries and includes claims of nearly one billion customer records, highlighting the potential impact of coordinated campaigns run under the Scattered LAPSUS$ Hunters name even before ShinySp1d3r is fully deployed.
At this point the ShinySp1d3r RaaS remains in development. Initial claims from Scattered LAPSUS$ Hunters suggest that the ransomware will have a modular framework with a Windows encryptor and planned Linux and VMware ESXi variants. The group’s messaging references ongoing testing, but there are currently no publicly confirmed instances of the ransomware being deployed.
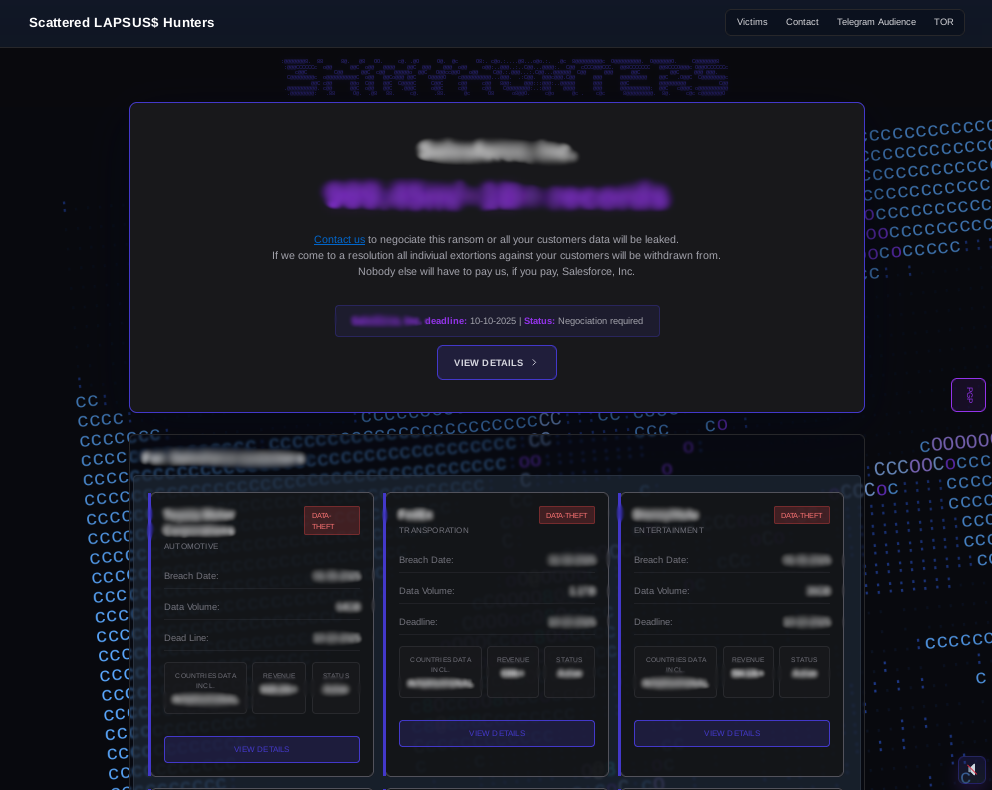
Figure 1: Redacted Scattered LAPSUS$ Hunters data leak site.
In recent years, Scattered Spider, LAPSUS$, and ShinyHunters have each carried out high impact data theft, extortion, and ransomware related activity against large enterprises across multiple sectors. MOXFIVE has supported investigations involving Scattered Spider and ShinyHunters that reflect the social engineering, identity abuse, and data theft we can expect to see from the Scattered LAPSUS$ Hunters alliance. Collaboration between threat actor groups is common, but it is alarming to see three of the most capable English-speaking threat actor groups publicly aligning on Telegram, sharing leak infrastructure, and promoting a dedicated ransomware operation under a single name.
Key Takeaways:
While ShinySp1d3r has not yet been observed in victim environments, MOXFIVE is closely monitoring its development and related SLSH activity as this threat evolves into 2026.
Given the advanced nature of the threat actors behind the groups that make up Scattered LAPSUS$ Hunters, a new ShinySp1d3r RaaS could quickly become a high impact ransomware threat if development progresses as described. Initial claims indicate that the ransomware is being designed as a modular family with a Windows encryptor and planned Linux and VMware ESXi variants. Communication from the group describes a custom-built encryptor with options to tune how aggressively it runs, what it targets, and how victims are notified. Most of the current details come from threat actor messaging on the leak site and ongoing Telegram activity.
The Scattered LAPSUS$ Hunters Telegram channel mixes claims about ShinySp1d3r and recent compromises with taunts, threats, and trolling content. The channel provides a running view of how the alliance presents the ransomware and its own operations, but individual claims need to be weighed against technical evidence and incident reporting before they are treated as fact.
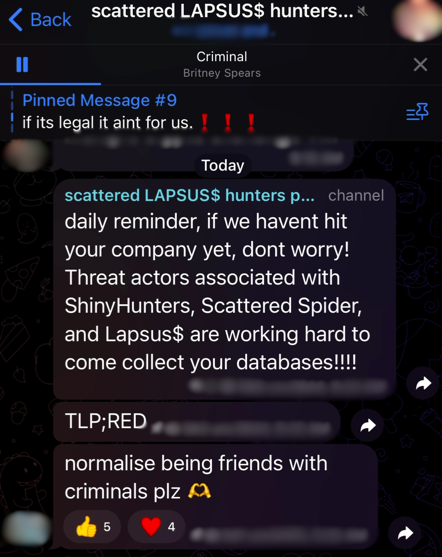
Figure 2: SLSH Telegram channel.
Telegram posts and public reporting suggest that the ransomware will include several additional features if development continues as stated, including:
Based on current information, ShinySp1d3r should be treated as ransomware that is still in development and primarily visible through Scattered LAPSUS$ Hunters communications, rather than a RaaS family with broad, confirmed deployment. The concern is that a custom encryptor with stated plans for ESXi support, combined with SLSH’s existing history of social engineering, identity compromise, and extortion, could increase the impact of future compromises if the service matures and is used more widely.
The Threat Actors Behind the Scattered LAPSUS$ Hunters Alliance
Scattered LAPSUS$ Hunters presents itself as an alliance of three established threat groups: Scattered Spider, LAPSUS$, and ShinyHunters. Each group has its own history, tradecraft, and victim profile, and together they help explain why a future ShinySp1d3r RaaS operation would pose a significant risk to large enterprises.
Scattered Spider
Scattered Spider is a decentralized group of threat actors also tracked as UNC3944, Star Fraud, Muddled Libra, Octo Tempest, and Scatter Swine. Active since at least 2022, the group is known for social engineering of IT help desks, SIM swapping, MFA fatigue attacks, and abuse of cloud identity and remote access. Its operations have included high profile intrusions at large hospitality and gaming firms where, in some cases, Scattered Spider worked with established ransomware programs to deploy ransomware after gaining access. For more information visit the MOXFIVE Threat Actor Spotlight – Scattered Spider.
LAPSUS$
LAPSUS$ is an extortion focused threat group that first appeared in 2021 and is known for intrusions at large technology and telecom firms. The group operated largely in public through Telegram channels, leaking source code and internal data, posting victim polls, and recruiting insiders for credentials and multi factor authentication codes. Documented techniques include SIM swapping, MFA fatigue, and direct payments to employees for one-time passwords or VPN access. Law enforcement actions in 2022 reduced visible LAPSUS$ activity.
ShinyHunters
ShinyHunters is a financially motivated threat group that first gained attention in 2020 by advertising large data sets from compromised online services and technology platforms. Over time, the group has been linked to breaches affecting marketplaces, telecom providers, and other cloud hosted environments, often focused on bulk theft of customer and account data for resale or extortion. This history of broad data theft and public leaks aligns with the emphasis on stealing and exposing sensitive information that Scattered LAPSUS$ Hunters now claims under the alliance.
Mitigation Considerations
Ransomware and intrusion activity continue to evolve as new threats emerge, and attacker automations shorten timelines. A developing RaaS operation like ShinySp1d3r, backed by the Scattered LAPSUS$ Hunters alliance, reinforces the need for a focused set of controls that consistently reduces impact across both established and emerging threats.
Critical Controls for Modern Resilience:
What We Are Watching:
Recommended Tabletop Scenarios:
End of Year Priorities:
Top Playbooks to Have Ready:
How MOXFIVE Can Help
Preparing for this threat means validating that identity, endpoint, network, and backup controls work together under stress, and that leadership teams know how they will respond if confronted with data theft, extortion, or encryption linked to groups like SLSH.
MOXFIVE supports organizations with control validation, resilience assessments, response playbook development, realistic tabletop exercises, exposure reduction, and backup and recovery testing. Our team aligns preventive, detective, and recovery controls to current ransomware and intrusion trends to strengthen resilience across modern enterprise environments. Contact us at 833-568-6695 or email our team directly at incident@moxfive.com.