July saw an increase in ransomware activity compared to the previous summer months, with Inc. ransomware ranked as the most deployed variant based on leak site postings. Akira and Qilin also maintained steady operations, contributing to consistent impact across multiple industries. The Technology sector stood out as the most targeted, with ransomware activity impacting software-as-a-service providers and other technology-focused organizations.
The month also brought notable exploitation events. Activity against SonicWall SSL VPN appliances, initially believed to be a zero-day, was linked to CVE-2024-40766, while a zero-day vulnerability chain in on-premises SharePoint servers was actively leveraged by multiple threat actors and is detailed in this month’s Case Study and Resilience Spotlight.

Phishing emails, VPN vulnerabilities, lack of Multifactor Authentication (MFA), software flaws, drive-by downloads, and social engineering remain the most frequently observed initial access points for ransomware attacks.

Overall, ransomware activity increased in July compared to the previous summer months. Inc., a group that might be surprising to see at the top of the activity charts, was the most deployed ransomware this month based on leak site postings.
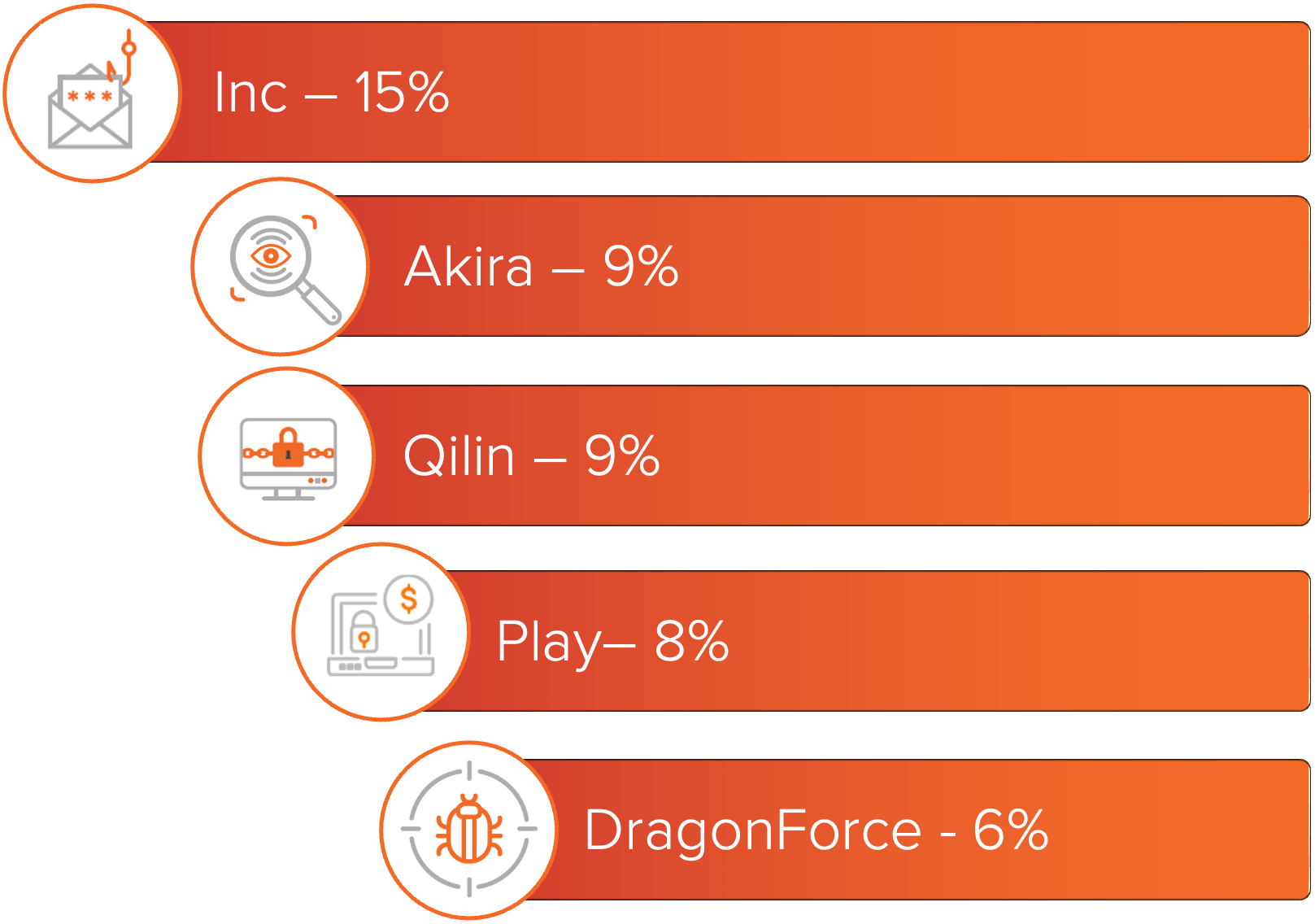
Figure 1: Top ransomware variants based on number of known victims.
The ransomware and industry rankings below are based on observed ransomware data leak site (DLS) activity for impacted organizations in the United States.
For a deeper look into these groups, MOXFIVE has published Threat Actor Spotlights on Qilin, Akira, Play, and DragonForce.

The Technology sector was the most impacted sector throughout July, with the other industries being relatively balanced when looking at impacted victims.
Healthcare ranked second after leading in June. Manufacturing and Production, Professional Services, and Construction and Engineering also ranked among the top targeted industries, reflecting the continued spread of ransomware across critical services, infrastructure, and institutions.
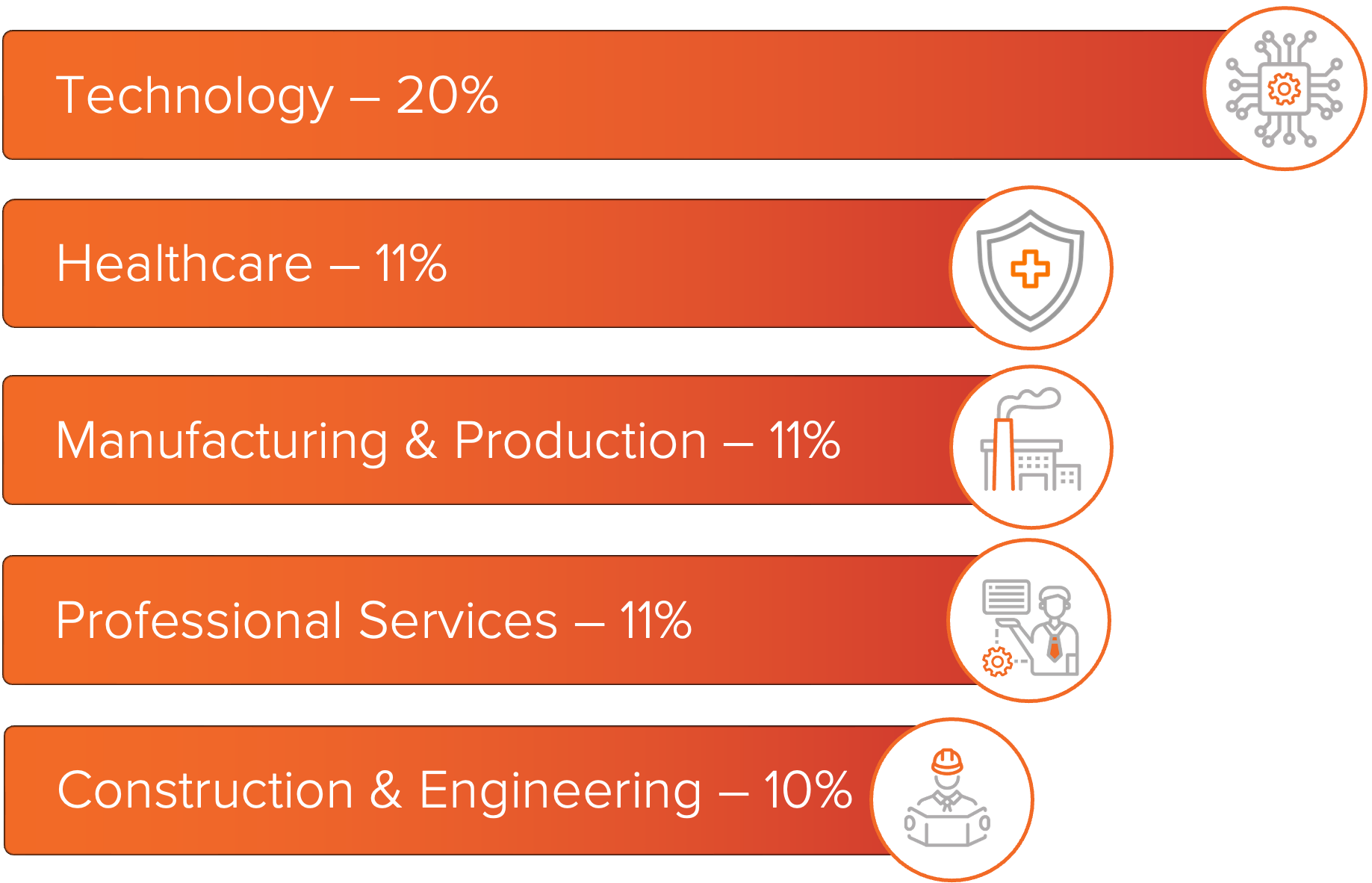
Figure 2: Top industries impacted by ransomware this month.

SharePoint Zero-Day Exploitation
In July, a zero‑day vulnerability chain in on‑premises SharePoint servers was exploited in the wild. The chain combines CVE‑2025‑49704 (remote code execution) and CVE‑2025‑49706 (spoofing) for initial access, with later patch‑bypass variants CVE‑2025‑53770 and CVE‑2025‑53771 related to the original pair. Activity began no later than July 7th before fixes were available on July 8th. Impact is limited to SharePoint Server 2016, 2019, and Subscription Edition. SharePoint Online is not affected.
Microsoft advised organizations to run supported versions, apply the new security updates without delay, then rotate ASP.NET machine keys and restart IIS. Enabling AMSI with antivirus protection on SharePoint servers and using an endpoint detection and response solution were also recommended. For more details on this exploitation and IOCs, visit the Microsoft report here.
Exploitation: Microsoft has assessed that multiple threat actors have exploited these vulnerabilities, including Chinese state actors Linen Typhoon and Violet Typhoon. Microsoft also observed Storm‑2603, assessed with moderate confidence to be China‑based, using this access to deploy Warlock ransomware via Group Policy.
For additional details concerning this zero-day vulnerability, including a list of possible indicators of compromise (IOCs), visit Microsoft’s report here.

Defending Against Zero-Day Exploitation of Internet-Exposed Apps
Zero‑day flaws in internet‑exposed collaboration and web applications turn common platforms into viable entry points. The SharePoint activity this month is one example. The priorities are to reduce exposure, remove persistence opportunities where supported, and detect post‑exploit behavior quickly and reliably.
MOXFIVE supports organizations working through zero‑day exposure, ransomware activity, recovery, and forensics, and can help translate these controls into an actionable roadmap for your environment.
If you missed our Mid-Year Ransomware Briefing where we covered the latest developments and key trends for cyber incidents so far this year, it's not available online. Watch Now >>
Need Help Now? Whether you need help responding to an incident or are just trying to better prepare for one, we can help. Contact us at 833-568-6695 or email our team directly at incident@moxfive.com.