November was another busy month for ransomware activity, with Akira remaining one of the most frequently deployed variants and Cl0p’s Oracle E-Business Suite extortion campaign now reflected in data leak site postings. Overall volume was slightly lower than in October but remained higher than in previous months. Manufacturing and Production remained the most impacted industry, followed by Technology, Healthcare, Retail and Hospitality, and Professional Services.
This month’s report covers exploitation of the CentreStack deserialization vulnerability CVE-2025-30406, which MOXFIVE observed being used to deploy Warlock ransomware. It also outlines the React2Shell remote code execution issue in React Server Components (CVE-2025-55182). The Case Study examines how exposure of internet-facing file-sharing platforms can lead to ransomware deployment. The Resilience Spotlight focuses on practical controls for hardening these services, supporting timely vulnerability management, and strengthening detection around file-sharing and collaboration infrastructure.
Phishing emails, VPN vulnerabilities, lack of Multifactor Authentication (MFA), software flaws, drive-by downloads, and social engineering remain the most frequently observed initial access points for ransomware attacks.
Overall ransomware volume slightly decreased in November compared to October but remained higher than previous months. Ransomware groups that operate under a ransomware-as-a-service (RaaS) model continue to drive a significant portion of activity through widespread affiliate deployment. The impact of the Cl0p Oracle E-Business Suite extortion campaign is starting to be seen as more than 100 organizations have been added to its leak site between late October and November.
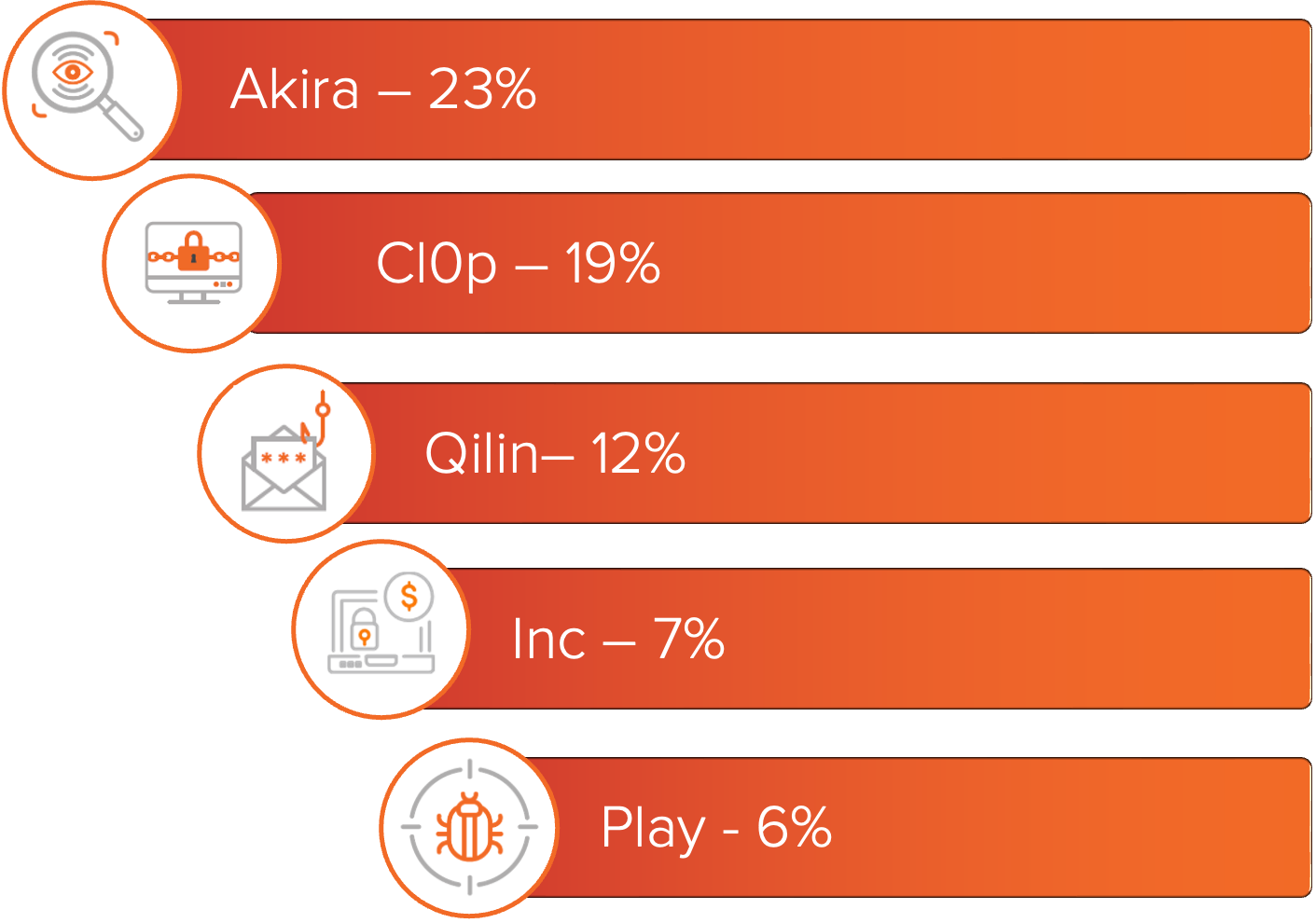
Figure 1: Top ransomware variants based on number of known victims.
The ransomware and industry rankings below are based on observed ransomware data leak site (DLS) activity for impacted organizations in the United States.
For a deeper look into these groups, MOXFIVE has published Threat Actor Spotlights on Qilin, Akira, Inc, and Play.
Manufacturing and Production remained the most impacted industry in November, continuing a trend observed throughout 2025. Threat actors continue to target this sector due to the high impact that business interruption can have and the use of connected supply chains that create multiple paths for initial access. Technology was the second most impacted industry, as service providers and software platforms often maintain direct integration with client networks and cloud environments, increasing the potential impact of a single intrusion.
Healthcare, Retail and Hospitality, and Professional Services also saw consistent ransomware activity in November. Healthcare organizations remained attractive targets due to the sensitivity of patient and
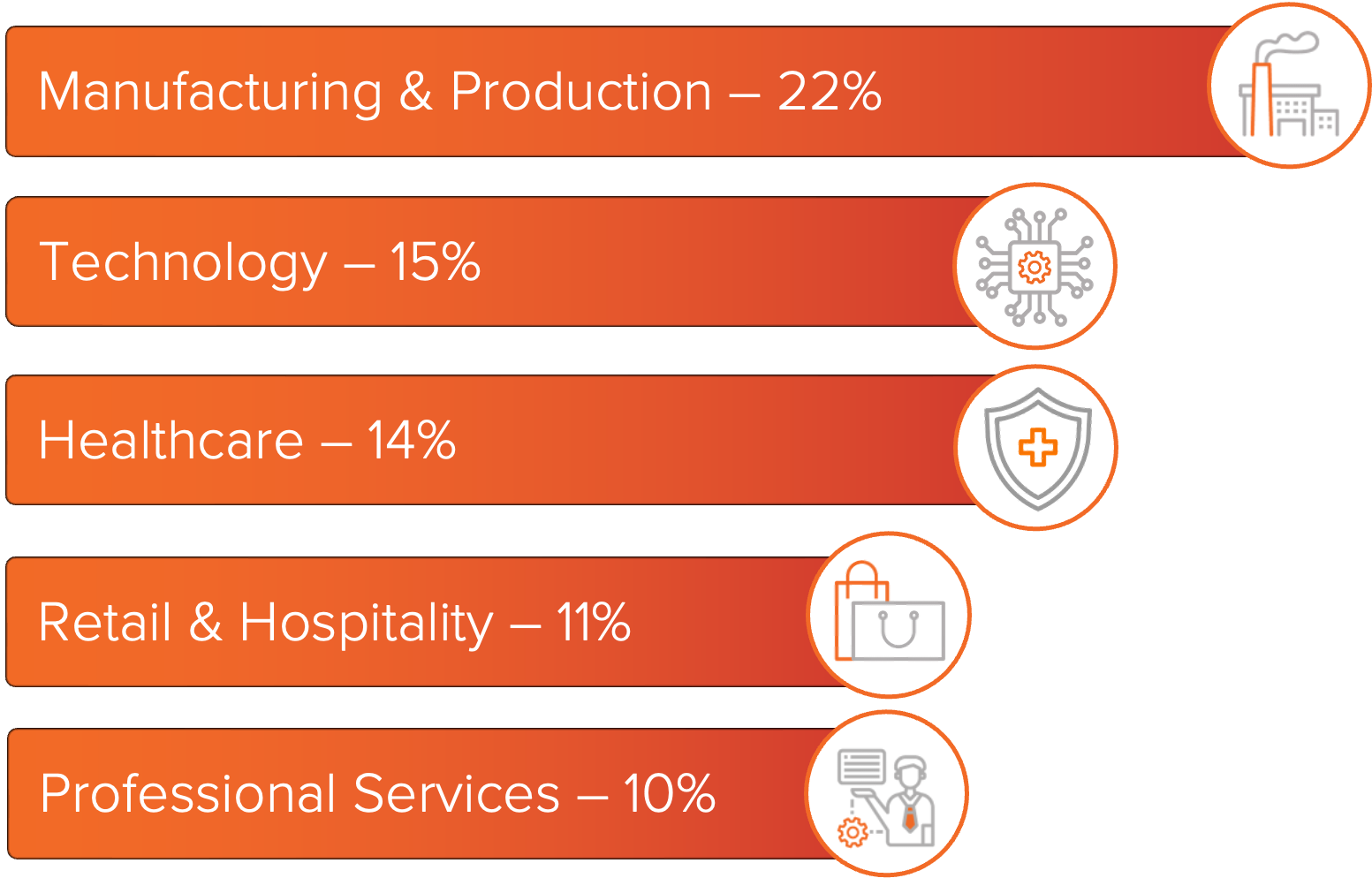
Figure 2: Top industries impacted by ransomware this month.
operational data and their limited tolerance for sustained outages. Retail and Hospitality incidents often involved organizations that process payment data or operate distributed physical locations, exposing point-of-sale systems and supporting infrastructure. Professional Services firms continued to be targeted because compromise of a single provider can expose multiple client environments and sensitive client data.
Across these industries, Akira was a primary driver of incidents in Manufacturing and Production, with Qilin and Play also frequently observed impacting that sector. Akira activity was also prominent in Retail and Hospitality cases. Among victims of the Cl0p Oracle E-Business Suite campaign, Technology organizations make up the highest percentage of victims, although the campaign impacted entities across most of the industries shown in Figure 2.
In November, MOXFIVE observed threat actors exploiting the CentreStack deserialization vulnerability CVE-2025-30406, which can allow unauthenticated remote code execution on internet-facing file-sharing portals and provide a path to deploy Warlock ransomware. The vulnerability stems from a hard-coded ASP.NET machineKey in affected CentreStack portals, which can enable forged ViewState payloads and arbitrary code execution until patched builds released in April 2025 are applied.
Warlock is a ransomware and extortion operation first observed in 2025 that operates under a ransomware-as-a-service model. Microsoft has associated Warlock deployments with the financially motivated threat actor it tracks as Storm-2603, assessed to be China-based, which has exploited Microsoft SharePoint ToolShell vulnerabilities to gain pre-authentication remote code execution on internet-facing servers. In these campaigns, the threat actors deploy web shells, move laterally, and in some cases launch multiple ransomware families, including Warlock and LockBit, before exfiltrating data and pressuring victims through a dedicated data leak site.
Figure 3: WarLock Data Leak Site.
The recent Warlock activity involving the CentreStack vulnerability shows how an unpatched, internet-facing file-sharing portal can provide direct access for ransomware deployment and large-scale data theft months after a fix is available. Warlock campaigns linked to Storm-2603 have also involved deployment of other families such as LockBit, and this type of initial access can be leveraged by threat actors to deploy a range of ransomware payloads rather than a single variant. Resilience in this environment depends on a focused set of controls that reduce the impact of vulnerability-driven operations across both established and emerging threats.
How MOXFIVE Can Help
MOXFIVE supports organizations with control validation, resilience assessments, response playbook development, realistic tabletop exercises, exposure reduction, and backup and recovery testing. Our team aligns preventive, detective, and recovery controls to current ransomware and intrusion trends to strengthen resilience across modern enterprise environments. Contact us at 833-568-6695 or email our team directly at incident@moxfive.com.