Ransomware activity increased in October, driven by heightened deployment of Qilin and steady operations by Akira, Inc, and Play. Qilin was the most active variant, benefiting from a growing affiliate base following the RansomHub takedown. Manufacturing and Production remained the most impacted industry, followed by Healthcare, Technology, Retail and Hospitality, and Professional Services. Activity in these sectors reflected continued targeting of organizations with operational dependencies and integrated vendor networks.
October also included active exploitation of multiple vulnerabilities, including the Oracle E-Business Suite zero-day (CVE-2025-61882) associated with Cl0p and the Fortra GoAnywhere Managed File Transfer (MFT) deserialization flaw (CVE-2025-10035) leveraged in Medusa campaigns. MOXFIVE also observed the emergence of several new ransomware variants including Tengu, Genesis, Radiant, and Kryptos, each launching data leak sites (DLS) and posting initial victims. These developments reflect continued turnover within ransomware operations and reinforce the importance of adaptable resilience across enterprise environments.
Phishing emails, VPN vulnerabilities, lack of Multifactor Authentication (MFA), software flaws, drive-by downloads, and social engineering remain the most frequently observed initial access points for ransomware attacks.
There was a considerable increase in ransomware activity in October compared to previous months. Much of that activity can be attributed to ransomware campaigns where Qilin was deployed. Among the most active variants, Qilin, Akira, and Inc operate as ransomware-as-a-service (RaaS) offerings, while Play and Sinobi operate as closed groups.

Figure 1: Top ransomware variants based on number of known victims.
The ransomware and industry rankings below are based on observed ransomware data leak site (DLS) activity for impacted organizations in the United States.
For a deeper look into these groups, MOXFIVE has published Threat Actor Spotlights on Qilin, Akira, Sinobi, Inc, and Play.
Manufacturing and Production was the most impacted industry in October, continuing a trend observed throughout 2025. Threat actors maintained focus on this sector due to the high operational impact of downtime and the use of connected supply chains that create multiple intrusion paths. Healthcare followed as the second most impacted industry, with reporting in October showing a shift from hospitals to healthcare vendors and service providers.
Technology, Retail and Hospitality, and Professional Services were also heavily impacted. Technology firms remained frequent targets because of their integration with client networks. Retail and Hospitality saw elevated targeting, with notable Sinobi activity observed against this sector. Professional Services continued to be targeted due to the potential for compromise to span multiple client environments.
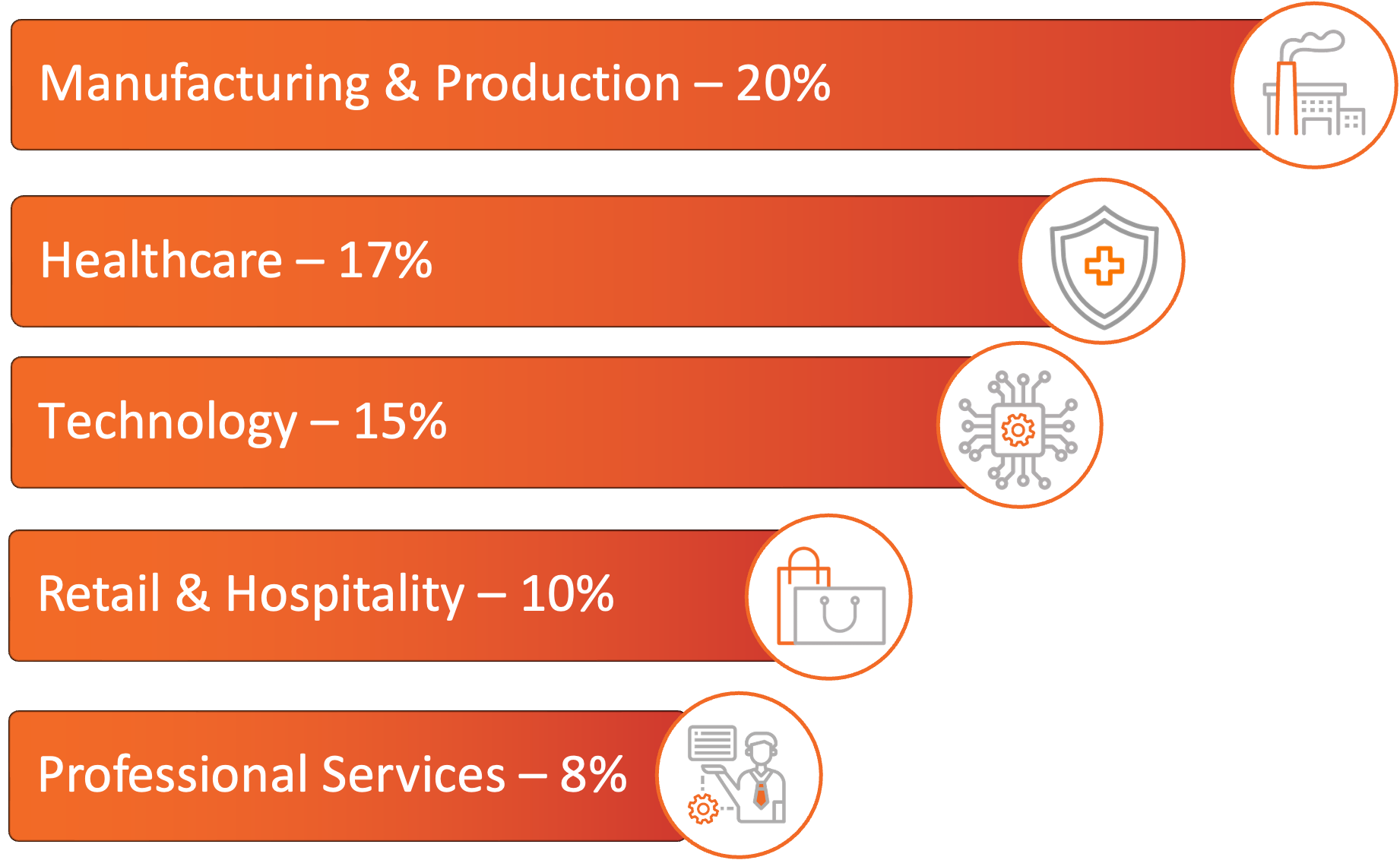
Figure 2: Top industries impacted by ransomware this month.
Across most sectors, threat actors deploying Qilin ransomware had the greatest impact on overall activity. Akira was also widely observed in the wild, but impact in October was concentrated in the Manufacturing and Production and Technology sectors. Threat actors deploying Sinobi primarily targeted Healthcare and Retail and Hospitality.
MOXFIVE tracked several new ransomware variants that entered the threat landscape in October, each launching a leak site and posting initial victims. New ransomware operations appear every month, whether through new threat actors entering the landscape, rebrands of defunct groups, or the resurgence of older operations. MOXFIVE has experience assisting with some of the earliest cases involving new groups and continues to track emerging operations and extortion methods to remain proactive in supporting incident response and resilience planning.
Ransomware and intrusion activity accelerated this month as new variants emerged, and AI-driven automation shortened attacker timelines. Resilience depends on a focused set of controls that consistently reduces impact across both established and emerging threats.
What We Are Watching:
Recommended Tabletop Scenarios:
End of Year Priorities:
Top Playbooks to have Ready:
How MOXFIVE Can Help
MOXFIVE supports organizations with control validation, resilience assessments, response playbook development, realistic tabletop exercises, exposure reduction, and backup and recovery testing. Our team aligns preventive, detective, and recovery controls to current ransomware and intrusion trends to strengthen resilience across modern enterprise environments. Contact us at 833-568-6695 or email our team directly at incident@moxfive.com.