Ransomware activity increased slightly in September, led by Akira and Play, which continued to account for a significant portion of observed incidents across multiple sectors. Inc, Qilin, and SafePay followed in overall activity, maintaining steady operations throughout the month. Manufacturing and Production, and Technology were the most impacted industries, reflecting continued targeting of organizations with complex vendor ecosystems and operational dependencies.
September also saw continued exploitation of SonicWall SSL VPN appliances through CVE-2024-40766, primarily linked to Akira ransomware intrusions. The most significant development of the month was the exploitation of a zero-day vulnerability in Oracle E-Business Suite (CVE-2025-61882) by threat actors associated with Cl0p. The campaign involved widespread data theft and extortion targeting enterprise environments, consistent with Cl0p’s history of exploiting high-impact software vulnerabilities.
Phishing emails, VPN vulnerabilities, lack of Multifactor Authentication (MFA), software flaws, drive-by downloads, and social engineering remain the most frequently observed initial access points for ransomware attacks.
Overall, ransomware activity increased slightly in September compared to August. Akira maintained the top position, followed closely by Play. Groups like Akira, Inc, and Qilin all operate as a ransomware-as-a-service (RaaS) model and continue to be a popular option for affiliate threat actors looking to deploy ransomware.

Figure 1: Top ransomware variants based on number of known victims.
The ransomware and industry rankings below are based on observed ransomware data leak site (DLS) activity for impacted organizations in the United States.
For a deeper look into these groups, MOXFIVE has published Threat Actor Spotlights on Akira, Play, Inc, and Qilin.
Manufacturing and Production and Technology were the most impacted industries in September, each accounting for a significant portion of observed ransomware activity.
Healthcare ranked third, followed by Construction and Engineering and Professional Services. The distribution of activity across these sectors reflects the continued focus of ransomware operators on critical services and industries with high operational dependencies.
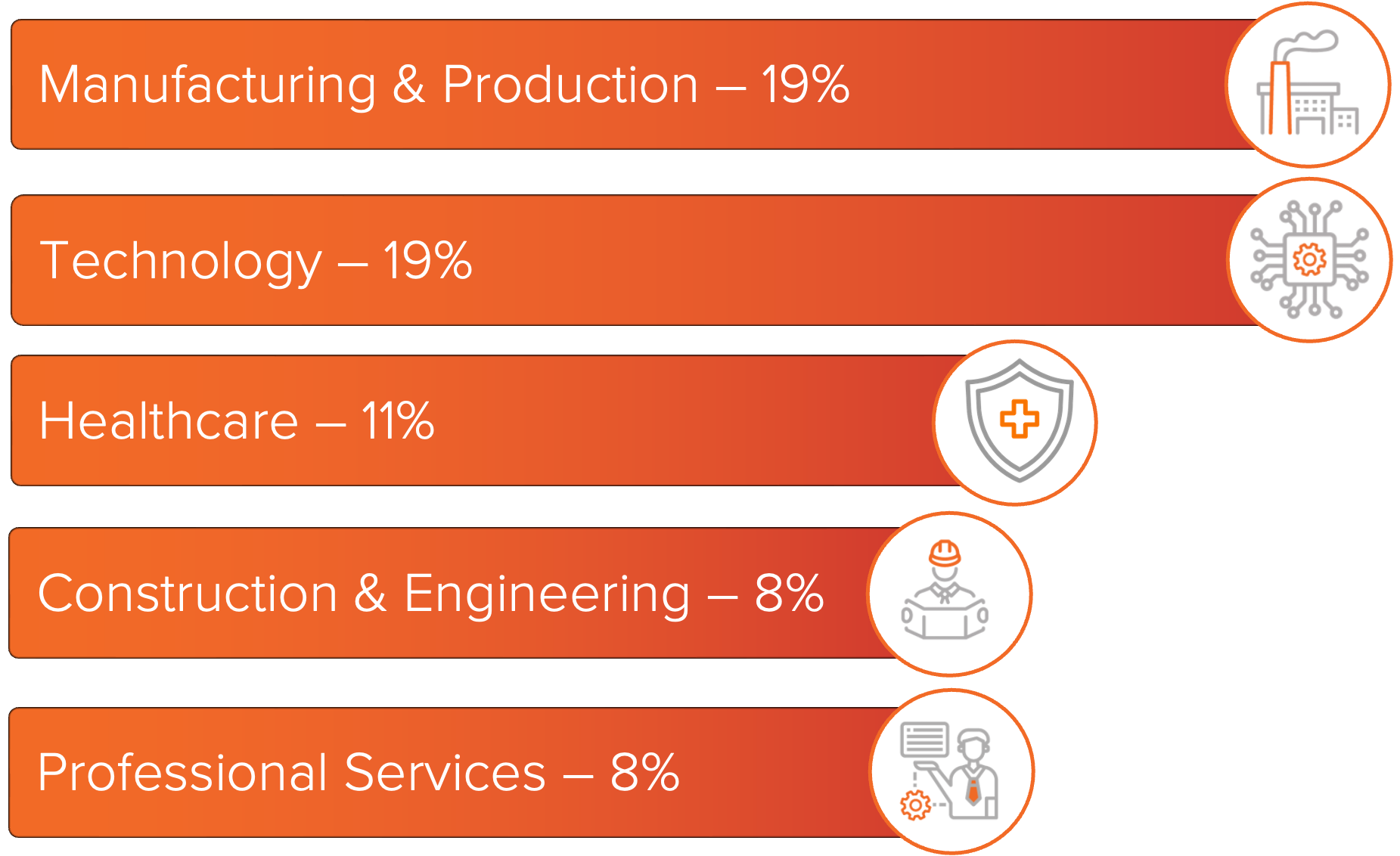
Figure 2: Top industries impacted by ransomware this month.
In late September, MOXFIVE observed a widespread extortion campaign conducted by threat actors associated with the Cl0p group. The threat actors sent a high volume of emails to organizations claiming to have accessed and exfiltrated data from Oracle E-Business Suite (EBS) environments. MOXFIVE published a Threat Actor Alert summarizing initial findings related to the campaign. Oracle later confirmed that it was a critical vulnerability, tracked as CVE-2025-61882, that allows unauthenticated remote code execution through the BI Publisher Integration component of the EBS Concurrent Processing product. The exploitation activity began as early as August, weeks before a fix was available, and targeted supported versions 12.2.3 through 12.2.14. Oracle released an emergency patch on October 4 and strongly recommends that customers apply all updates detailed in its Security Alert Advisory for CVE-2025-61882.
This activity reflects Cl0p’s established operational model, which centers on exploiting newly disclosed or unpatched vulnerabilities in enterprise software to enable large-scale data theft and extortion. Similar operations have included exploitation of MOVEit Transfer, GoAnywhere MFT, and Accellion FTA. In each case, Cl0p leveraged zero-day or near-zero-day vulnerabilities in business-critical systems to steal data from multiple organizations, later issuing coordinated extortion demands. The Oracle EBS campaign continues this pattern, demonstrating the group’s ongoing focus on vulnerabilities that allow pre-authentication access to high-value corporate data.
How MOXFIVE Can Help
The Oracle E-Business Suite campaign shows the importance of proactive patch management, controlled exposure of enterprise applications, and ongoing monitoring of public-facing systems. Threat actors associated with Cl0p exploited a remotely accessible, unauthenticated vulnerability before a patch was available, reinforcing the need for strong preventive and detection controls across enterprise environments.
If you missed our Mid-Year Ransomware Briefing where we covered the latest developments and key trends for cyber incidents so far this year, it's now available online. Watch Now >>
Need Help Now? Whether you need help responding to an incident or are just trying to better prepare for one, we can help. Contact us at 833-568-6695 or email our team directly at incident@moxfive.com.