Ransomware did not let up in 2025, new threats appeared, familiar operations shifted tactics, and exploitation-driven campaigns continued to turn single points of exposure into enterprise-wide impact. The year reinforced how quickly ransomware groups can scale when initial access is reliable and extortion pressure is consistent. This report summarizes what MOXFIVE observed across ransomware cases in 2025. It focuses on the most active variants, the initial access vectors that most often led to ransomware delivery, and the exploited vulnerabilities that drove distinct activity waves throughout the year.
Ransomware activity throughout 2025 was strongly influenced by ransomware-as-a-service (RaaS) operations, where operators provided the infrastructure and extortion framework to affiliate threat actors. Figure 1 shows the top five variants based on U.S. victims published to data leak sites (DLS) in the year. Akira, Qilin, and INC are the leading RaaS operations within this set, while Play and Cl0p appear to operate with a more closed model.
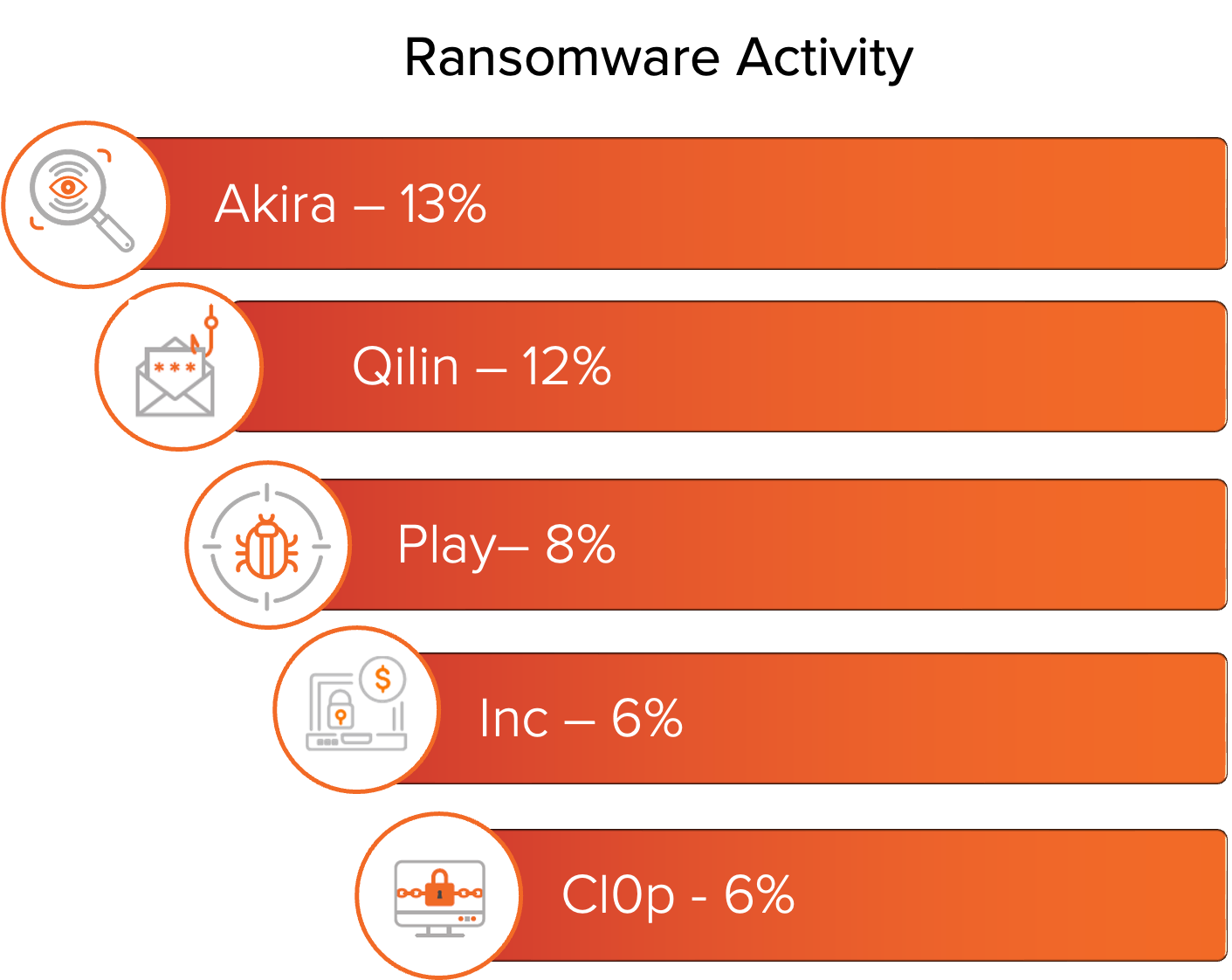
Figure 1: Top ransomware variants based on number of known victims.
Additional insights from MOXFIVE case work include early-year activity tied to RansomHub prior to its infrastructure being taken down in late March to early April. Interlock, first identified by MOXFIVE in September 2024, expanded operations throughout 2025 and demonstrated increased maturity in tradecraft and execution. MOXFIVE was also engaged in several Scattered Spider-linked campaigns throughout the year, consistent with social engineering-led initial access and rapid escalation following compromise. Later in the year, a Telegram channel titled as “Scattered LAPSUS$ Hunters” emerged and reportedly claimed ties spanning Scattered Spider, LAPSUS$, and ShinyHunters, reinforcing that this activity is being framed as an alliance built around shared tradecraft, joint extortion messaging, and a common goal.
Throughout 2025, ransomware campaigns showed consistent tactics, techniques, and procedures used to gain initial access. Based on MOXFIVE observations, remote entry points were the most common access paths, either through authenticated access or direct exploitation. Virtual private network (VPN) access was the most frequently observed starting point, followed by exploitation of internet-facing software or hardware vulnerabilities. Figure 2 breaks down the initial access vectors observed across ransomware cases, including exposed Remote Desktop Protocol (RDP) services, social engineering-driven access, and activity that led users to execute malicious downloads through lures such as phishing.
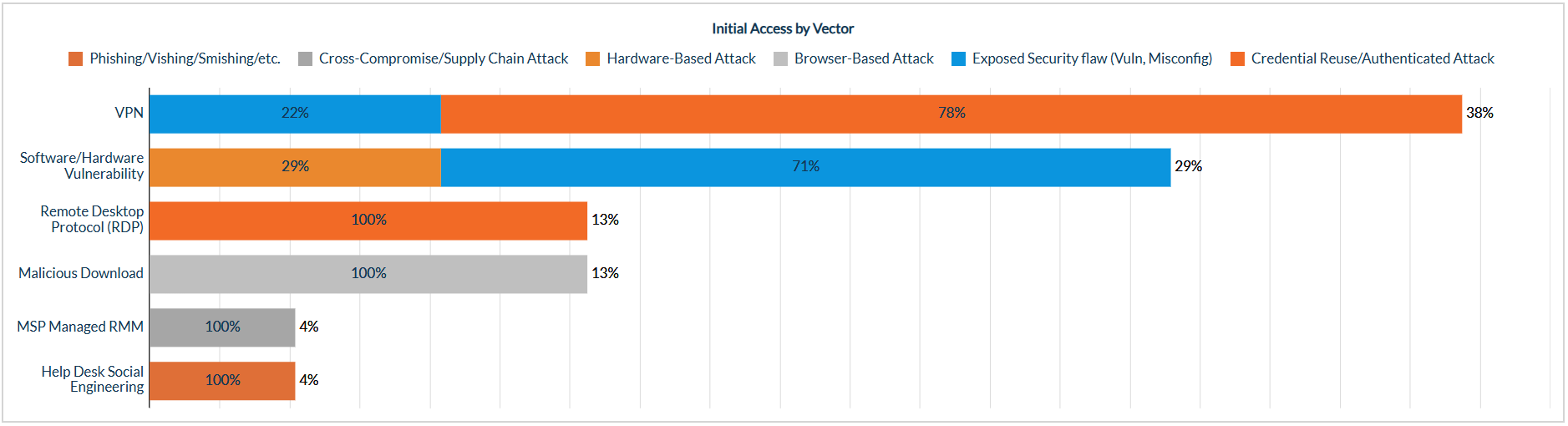
Figure 2: Initial access trends observed by MOXFIVE.
The exploitation of vulnerabilities remained a consistent driver of ransomware risk throughout 2025, particularly when flaws affected widely deployed remote access and enterprise application platforms. Organizations stayed exposed through a mix of zero-day exploitation, unpatched or delayed remediation after fixes were available, and repeat exploitation of older issues when upgrades or migrations carried forward insecure configurations. The vulnerabilities below show distinct exploitation waves across the year, with recurring patterns that included unauthenticated access paths and follow-on activity aligned to data theft and extortion.

Ransomware conditions heading into 2026 continue to favor affiliate-driven operations, with RaaS programs and access brokers sustaining a steady supply of campaigns built on remote access and identity-based entry points. Vulnerability exploitation is likely to remain a primary driver, particularly for edge and enterprise platforms that offer broad reach and high-impact access. Social engineering is expected to stay central for access and privilege escalation, with hdesk impersonation and identity workflow abuse continuing to generate reliable initial footholds. Key trends and emerging threats to track entering 2026 include:
How MOXFIVE Can Help
MOXFIVE supports organizations with control validation, resilience assessments, response playbook development, realistic tabletop exercises, exposure reduction, and backup and recovery testing. Our team aligns preventive, detective, and recovery controls to current ransomware and intrusion trends to strengthen resilience across modern enterprise environments. Contact us at 833-568-6695 or email our team directly at incident@moxfive.com.